
GuardWare gives organisations direct control of their sensitive information by binding encryption and usage policy to the data itself. It finds and labels critical and regulated content, tracks how it moves across teams and suppliers, and keeps it protected at rest, in transit, and while in use—so you can grant, limit, or revoke access on demand with verifiable evidence for assurance and audits. Vectra partners with GuardWare to help defence, utilities, and critical infrastructure lift Essential Eight maturity: we design and run rapid pilots, architect policies, harden configurations, and deliver production deployments with ongoing tuning and licensing support.

GuardWare is a data-centric security platform that binds encryption and usage policy to the information itself. It discovers and classifies sensitive data across IT/OT, monitors how it moves internally and with suppliers, and enforces persistent protection—at rest, in transit, and while in use. Teams can grant, limit, or revoke access on demand, automate hardened baselines, and generate tamper-evident evidence for audits and board reporting. The result: provable control of critical information, even outside your perimeter.

“Developed with Australia’s defence ecosystem to protect official-sensitive data across the supply chain—with data-in-use encryption, instant revoke, and audit-ready evidence.”
GuardWare is built and proven with Australia’s defence ecosystem, focusing on securing official-sensitive data across the entire supply chain. Recent Defence Trailblazer announcements highlight PROTECT’s data-in-use encryption and remote revocation to keep designs and mission data under control—even off-network and with partners.
Why this matters
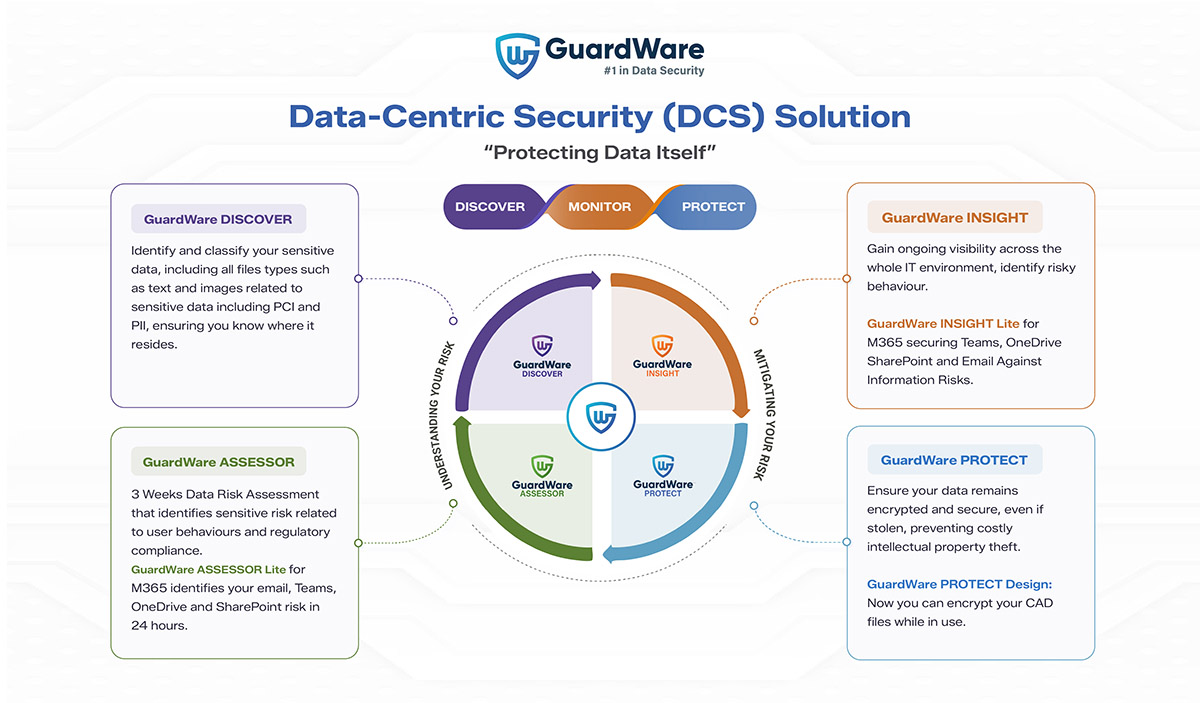
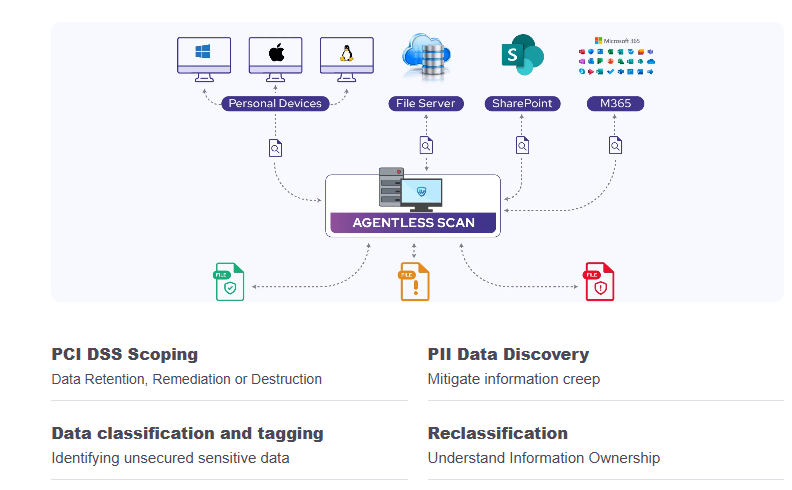
GuardWare Discover is the visibility engine of the platform: it finds your sensitive information wherever it lives, fingerprints it, and maps who can access it and how it moves—across M365, file shares, CAD/PLM, email, and OT data paths. It turns scattered files into a clear exposure picture and a prioritised hardening plan, ready for operations, audits, and board reporting.
GuardWare Assessor is the rapid-assessment module that measures how well your environment protects sensitive data today—and what to fix first. It evaluates configurations, access paths, and control coverage across M365, file shares, CAD/PLM and OT interfaces, then benchmarks results against Essential Eight and your internal policies to generate a clear, prioritised hardening plan.
Covers all channels and eliminates blind spots.
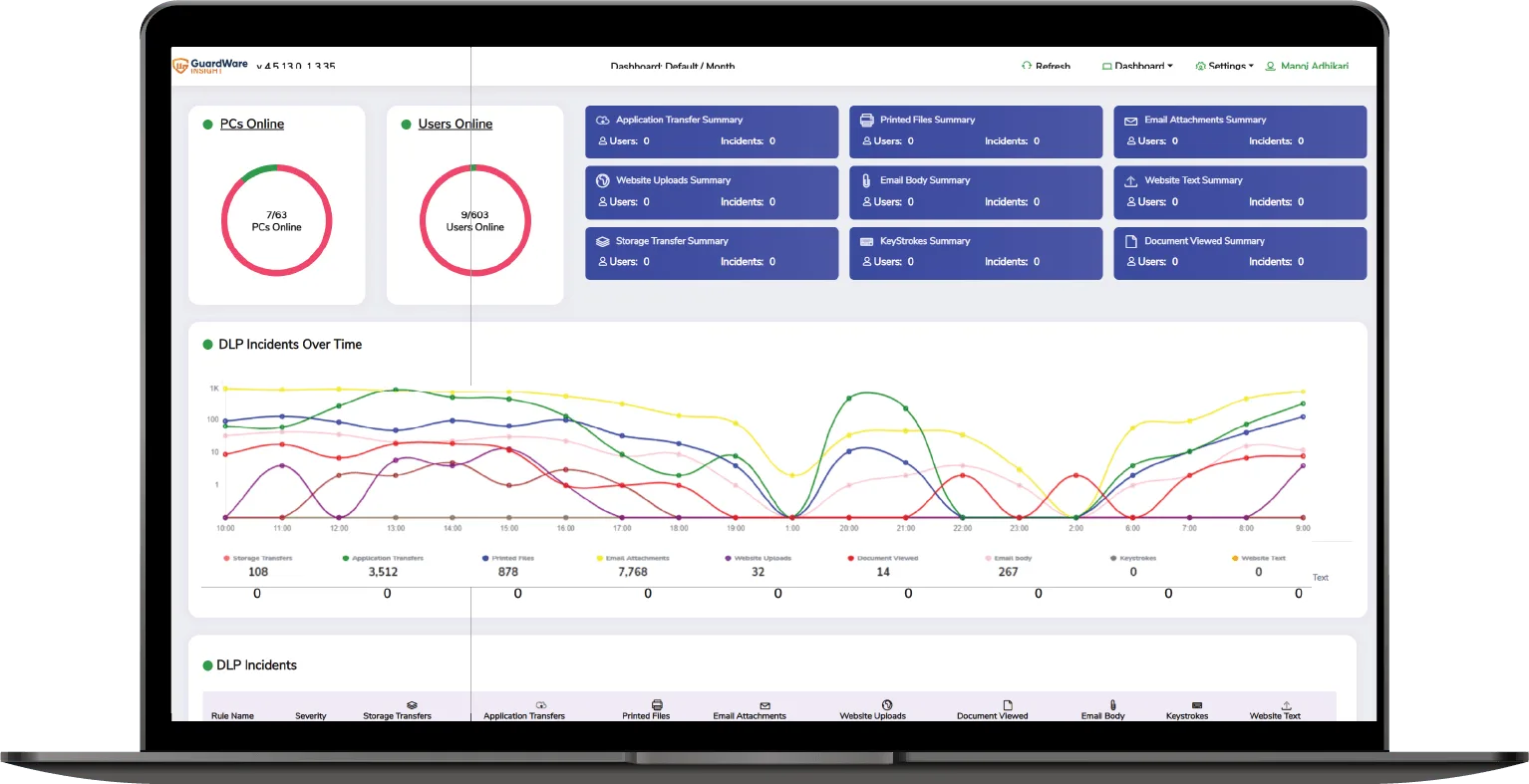
GuardWare Insight is the live telemetry and analytics layer that turns discovery data into operational awareness. It continuously tracks how sensitive files are accessed and moved, detects abnormal behaviour and policy drift, and surfaces the “so what” in clear dashboards and alerts. Insight plugs into your SIEM/SOAR and ticketing tools so the right team sees the right signal—fast—and action is captured for assurance and audits.
GuardWare Protect is the enforcement engine that binds encryption and usage policy to the data itself—so control stays with you anywhere the file goes. It applies least-privilege rules (view-only, watermark, block copy/print/export), enforces data-in-use encryption, and lets you revoke or time-limit access on demand across internal teams, contractors, and suppliers.
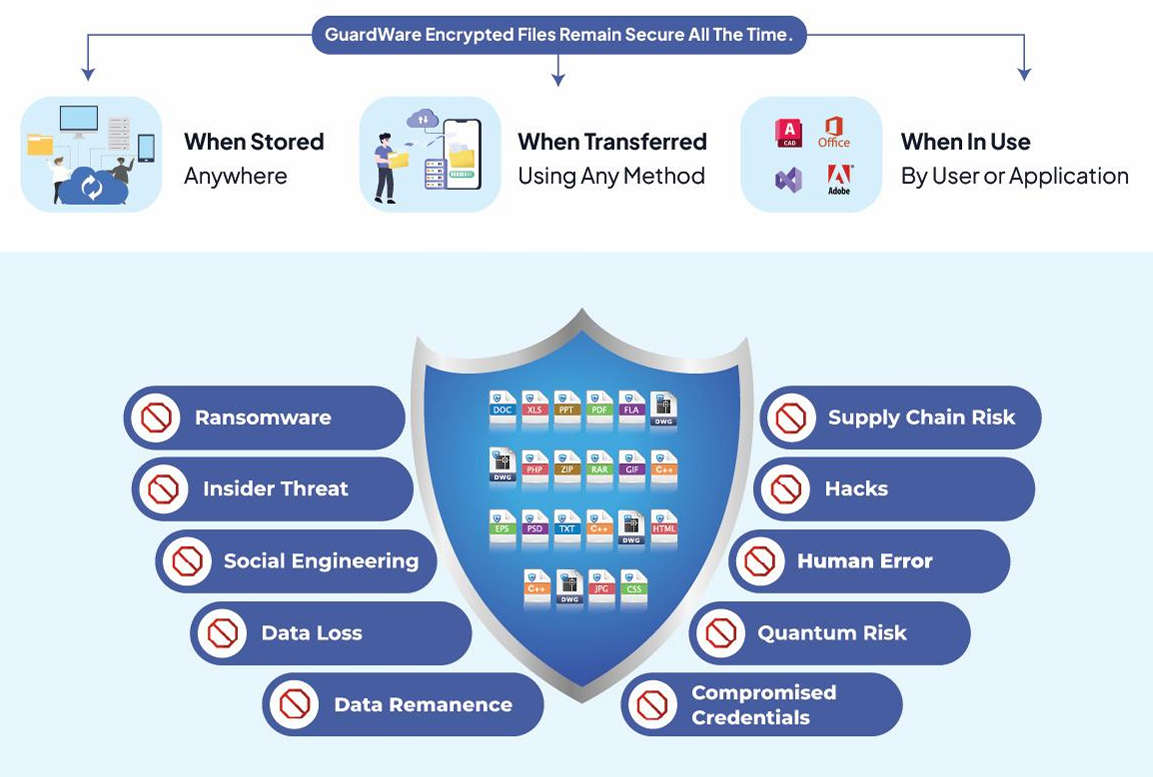
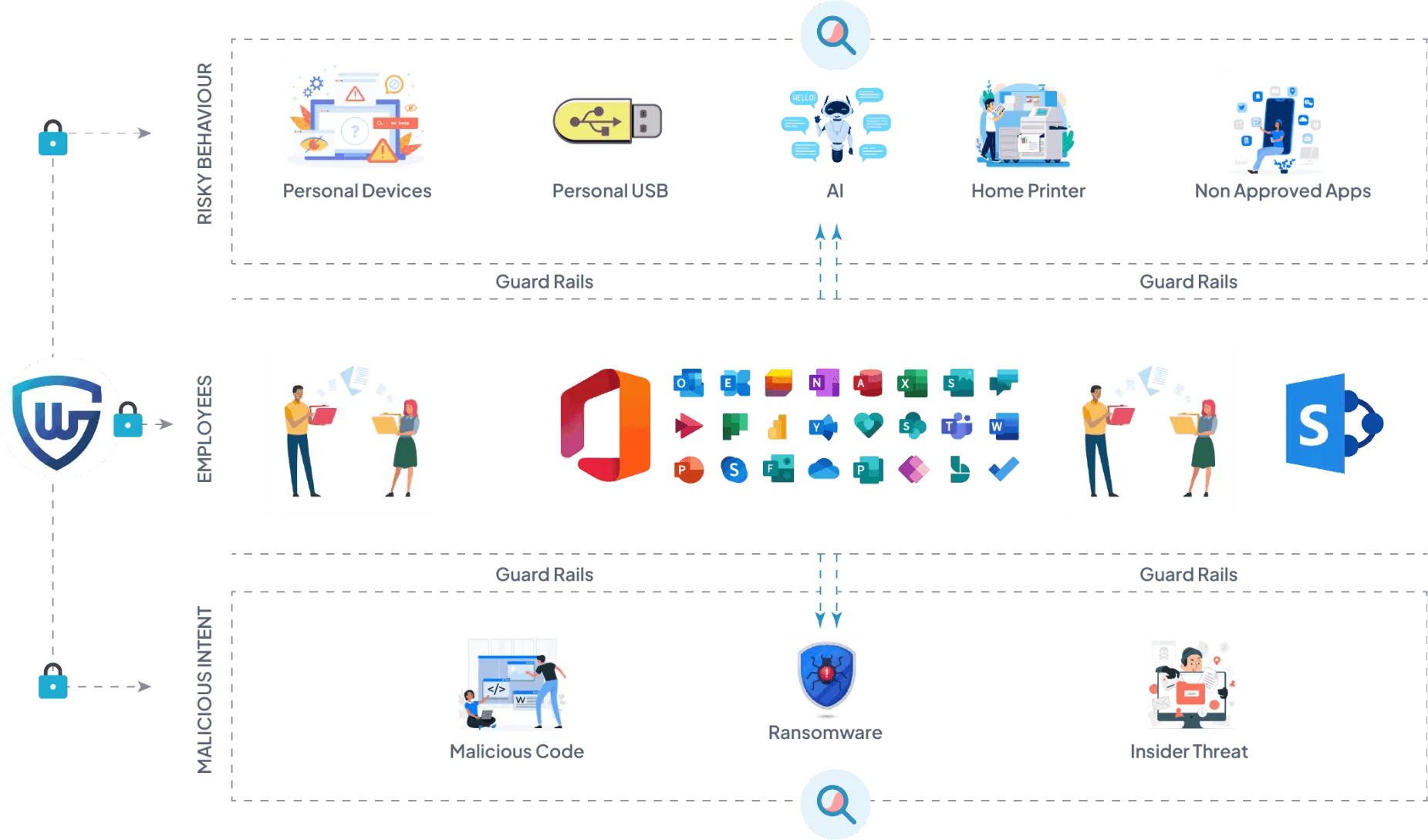
Traditional DLP focuses on stopping certain movements; once a file leaves, control is largely gone. GuardWare binds encryption and usage policy to the file itself—so even off-network and on supplier devices you can enforce view-only, watermark, no copy/print, expire, or revoke. It complements M365/IRM and CASB by adding persistent, data-in-use protection and supply-chain control.
No. We start monitor-only to map behaviour, then phase in policy (warn → enforce) where it won’t block the work. GuardWare integrates with M365/SharePoint, file shares, email, CAD/PLM and common OT hand-offs, so teams keep their tools while you gain control and visibility.
Yes. Controls travel with the file, not the network. You can set geo/time limits, offline grace windows, and revoke access instantly if risk changes (e.g., device fails posture checks, user off-boarded, incident declared). Tamper-evident logs show who opened what, where, and when—for primes, subs, and contracto
We run a rapid pilot to baseline exposure (GuardWare Discover/Assessor), integrate events to your SIEM/SOAR (Insight), then move to phased enforcement (Protect). Success is tracked via KPIs: reduction in uncontrolled shares/copies, time-to-revoke, policy coverage, and drift findings closed—mapped to ASD Essential Eight and your governance targets. Key management can be customer-managed or hosted escrow to meet compliance and residency requirements.
GuardWare supports customer-managed keys (your KMS/HSM, with separation of duties) or hosted key escrow in your chosen region. Policies ensure keys can be rotated, revoked, and audited, and protected content stays encrypted wherever it travels. Telemetry is minimised to what’s needed for assurance, with options for in-region processing and strict access controls to meet defence and critical-infrastructure requirements.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |